ABSTRACT
Extensible resource messaging in a communication network is provided through the creation of a flexible, extensible, and secure messaging environment
Extensible resource messaging in a communication network is provided by creating a flexible, extensible, and secure messaging environment.
A client-server architecture may be implemented in which user applications employ messaging clients to send resource requests for network information, allocation, and other operations and receive resource responses, and in which network elements, through resource agents, may use messaging servers to accept resource requests and return resource responses. Resource agents in different network domains may interact through the messaging environment and fulfill resource requests. An XML-based messaging mechanism may be built with a defined message format that can provide flexible message contexts. Network resource semantics may be specified using XML schemas to express network resources as resource-specific XML elements, and network updates can be implemented by updating the XML resource schemas. Secure enhancements may be realized by secure transport, message verification, and other means.
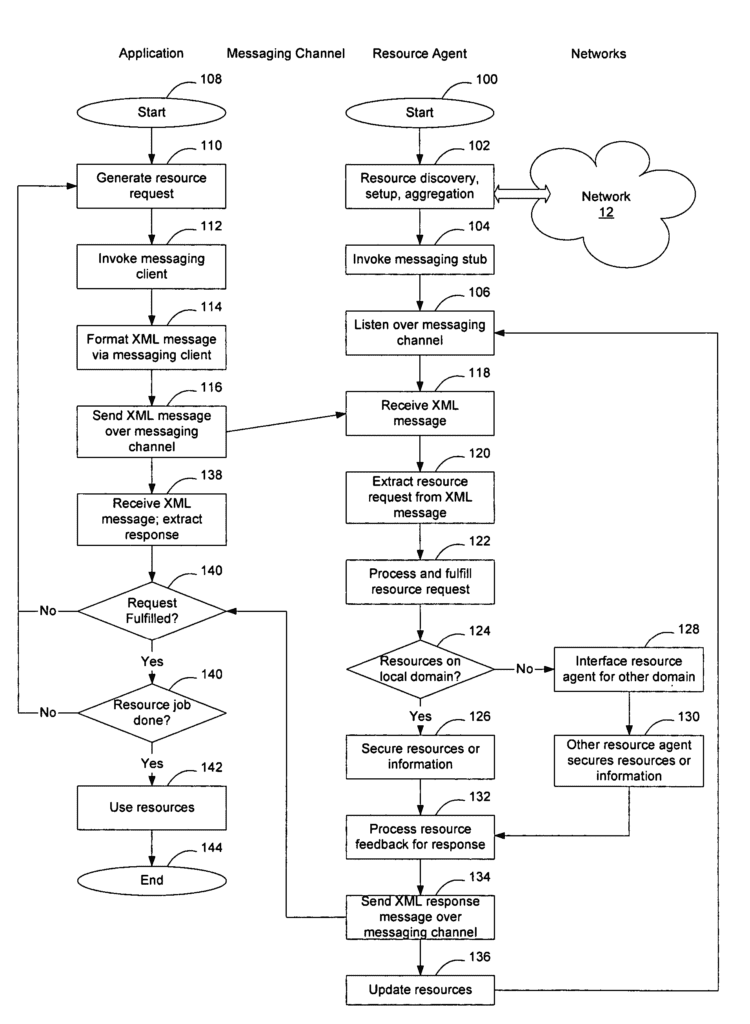
Extensible resource messaging between user applications and network elements in a communication network
An Inventor: Dr. Tal Lavian
BACKGROUND
1. Field
This application relates to communication networks and, more particularly, to extensible resource messaging between user applications and network elements in a communication network.
2. Description of the Related Art
Data communication networks may include various computers, servers, routers, switches, hubs, proxies, and other devices coupled to and configured to pass data to one another.
- Data communication networks may include various computers, servers, routers, switches, hubs, proxies, and other devices coupled to and configured to pass data to one another. These devices will be referred to herein as “network elements”. They may provide a variety of network resources, including physical resources such as communication links and bandwidths, and logical resources such as VPN (Virtual Private Network) and AAA (Authentication, Authorization, and Accounting) services. Conventionally, data has been transported through the data communication networks bypassing protocol data units (such as cells, frames, packets, or segments) between the network elements while utilizing one or more types of network resources. A protocol data unit may be handled by multiple network elements and cross multiple communication links as it travels between its source and destination over the network.
- Many user-end applications, such as grid computing, streaming media, and storage on demand require extensive network capability to obtain access to data, computational resources, storage resources, and other types of resources connected in a communication network. As communication networks have evolved, the type of applications designed to run on the network have also evolved and are expected to continue to evolve. To secure access to the resources connected by the network, the applications, therefore, communicate with network elements to obtain network resources to meet their requirements.
- Numerous protocols have been developed to allow network elements to communicate with each other and enable applications to communicate with network elements, several of which may be used by user applications to access resources on the networks. For example, Reservation Protocol (RSVP) may be used by Internet Protocol (IP) applications in a communication network, such as a statistical multiplexing packet-based network, to reserve a portion of the available bandwidth on the data transferring route through the network. Similarly, the User to Network Interface (UNI) allows an application to set up a traffic path, such as an ATM virtual circuit or an optical lightpath, over an ATM or optical transport network. However, those protocols are virtual network signaling protocols. They thus are defined to be used for pre-designated purposes such as to set up a network route and/or to perform link setup and teardown. Additionally, these protocols are generally defined by one or more standard bodies to enable interaction between the network elements. They are not explicitly designed to handle interactions between networks and applications. As new types of network resources continue to emerge on communication networks, how resource information is obtained and how resource utilization is obtained are important aspects to fulfilling application requests.
SUMMARY
Extensible resource messaging in a communication network is provided through the creation of a flexible, extensible, and secure messaging environment between user applications and network elements.
- According to an embodiment of the invention, extensible resource messaging in a communication network is provided by creating a flexible, extensible, and secure messaging environment between user applications and network elements. User applications are represented by resource clients that request information and/or the utilization of network resources. Network elements are represented by resource agents that manage and control access to and utilization of network resources. The messaging environment is flexible, according to one embodiment of the invention, because it may be implemented as an XML-based messaging mechanism. This mechanism contains a defined XML format that can provide flexible message contexts for resource requests and responses. Thus, applications can send XML messages to request network resource reservations and network discovery queries, and networks can send XML messages to respond to the application requests.
- The messaging environment is extensible, according to one embodiment of the invention, because it can introduce network resource semantics in terms of XML schemas. With the semantics, network resources can be added or removed through updating XML schemas. Thus, applications can easily use new network resources or avoid outdated network resources.
- The messaging environment is secure, according to one embodiment of the invention, because it may be built using secure transport technologies, including, for example, the exchange of digital signatures and certificates to authenticate the participating applications and networks or network agents. Through secure transport, messages from applications and networks may be encrypted and decrypted. Through digital identifications and certificates, applications can verify whether the networks have provided trustable information, while networks can authorize and even account resource utilization according to applications’ authentication.
- The messaging environment may be implemented using a client-server computer architecture. One or more messaging servers are implemented on the network to accept requests from applications. One or more messaging clients are created for resource applications requiring access to network resources. One or more resource agents may be associated with the messaging servers to realize network resource allocations on underlying networks or network domains. Optionally, one or more resource agents may also work with other resource agents to allow resource allocations and information. Obtained from other networks, with resource optimization when possible.