ABSTRACT
The invention provides a system and method for providing security against unauthorized access to a java enabled network device.
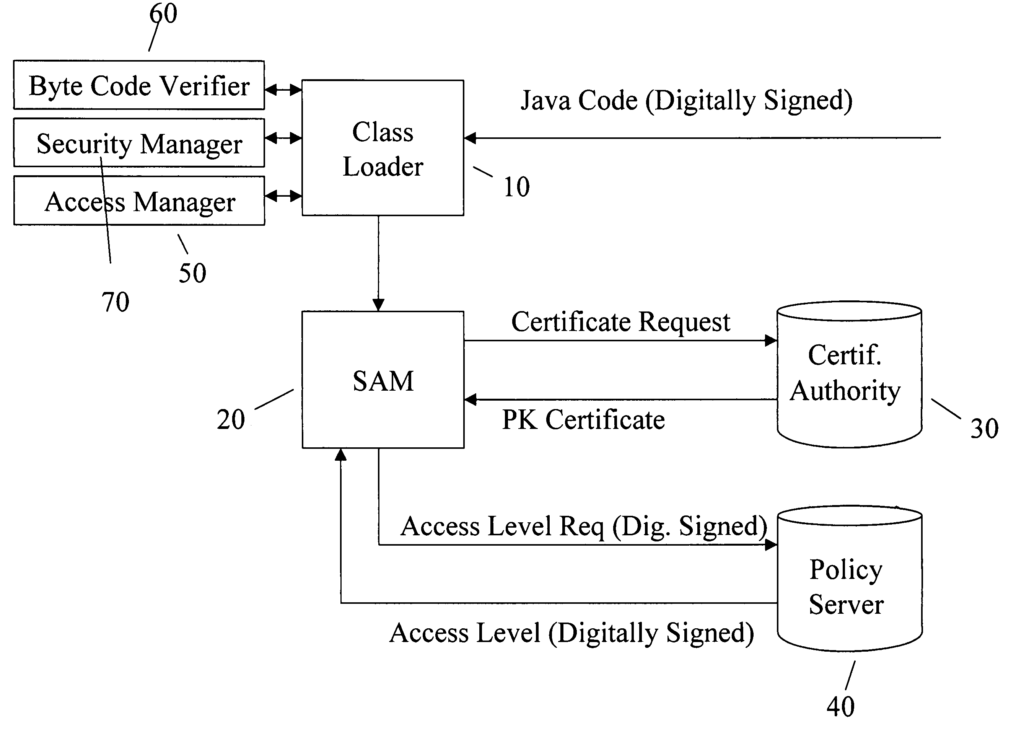
The system includes multiple conventional class loaders, code verifiers, security managers, access managers, SAMs, a certificate authority and a policy server. The SAM verifies the authenticity of the entity and either allows a download/access to a device or rejects the download/access to a network device. The certificate authority is a repository for public key certificates and may be a part of the secure network or part of the unsecured network. The policy server is a repository for the rights (privileges) an entity is entitled to on the secure network. The code verifiers verify that the Byte Code is valid java code. The security manager is the conventional security manager. The class loader loads the code to the device and the access manager assigns access levels to each Java thread that is created.
Security association mediator for java-enabled devices
An Inventor: Dr. Tal Lavian
FIELD OF THE INVENTION
This invention relates generally to the field of networking and more particularly to methods and apparatus for transferring files between devices in a secure manner.
BACKGROUND OF THE INVENTION
Data networks have become an essential part of most businesses. With the advent and wide acceptance of the Internet they have become even more essential.
Many network systems, such as telephone network products, data network products, etc. include externally developed software applications that call various functions within the network. It is desirable, however, to limit the functions and/or information that can be called by the application or the visitor to those that are necessary and/or approved.
It is thus important for a business to take precautions against downloading a code which may be potentially damaging to its network (e.g. a code which accesses the internal resources of a switch or router, such as the routing tables or filtering information, etc) and to take precautions against unauthorized access by outsiders.
It is unlikely that computers which access the Internet will ever be completely safe from attack from hackers and viruses. However, systems are available which provide a level of protection and security against such problems.
The Java environment includes security devices such as a security manager, a byte code verifier and a class loader. A security manager is a local device which determines whether potentially threatening or unauthorized operations should be allowed. A byte code verifier verifies the byte code transmitted with the download, and the class loader loads the Java Byte code to the JVM.
However, the security devices of a respective environment may not be backward compatible with earlier versions. In the Java environment, as an example, the security devices in version 1.2 are not backward compatible with those in versions 1.1 and 1.0.2, and the security devices in version 1.1 are not backwards compatible with those in version 1.0.2. Thus, an application program written in a respective version of Java is not compatible with other versions.
Furthermore, in some programming environments, such as in the Java environment, the security devices provide multi-level security but are not transparent, namely the user code must explicitly interact with the system, and the security devices are not dynamic, namely that off-line changes to the system may be necessary. Alternatively, the security devices are code transparent but do not provide multi-level security.
Accordingly, there exists a need for a security system which is system wide which prevents harmful programs from being downloaded onto a network.
There exists a need for a security system which is system wide and which prevents unauthorized access to the internal resources of a switch or router.
There also exists a need for such a system which enables a system view or configuration.
There also exists the need for such a system which is distributed.
There exists a need for such a system which allows other security entities to participate in the security system.
Accordingly, it is an object of the present invention to provide a security system which prevents harmful programs from being downloaded onto a network.
It is an object of the invention to provide a security system which prevents unauthorized access to the internal resources of a switch or router.
It is another object of the invention to provide such a system which is system wide and which enables a system view or configuration.
It is still another object of the invention to provide such a system which is distributed.
It is another object of the invention to provide a such a system which allows other security entities to participate in the security.
These and other objects of the invention will become apparent to those skilled in the art from the following description thereof.
SUMMARY OF THE INVENTION
In accordance with the teachings of the present invention, these and other objects may be accomplished by the present invention, which provides a method for providing security against unauthorized access to internal resources of a network device.
The method includes receiving a digital signature at a security association manager (SAM) wherein the digital signature includes an encryption code. The SAM requests a de-encryption code, de-encrypts the digital signature with the de-encryption code, authenticates the de-encrypted digital signature, and requests allowed operations associated with the authenticated signature.
An embodiment of the invention includes apparatus for providing security against unauthorized access to internal resources of a network device. The apparatus includes a security association manager (SAM) configured to receive a digital signature including an encryption code. The SAM is configured to send a message including a portion of the digital signature. The message includes a request for an encryption decoder. The SAM is further configured to receive a response to the message. The SAM is also configured to send a digitally signed message requesting allowed operations associated with the digital signature in response to receiving the reply message.
Another embodiment of the invention includes apparatus for providing security against unauthorized access to internal resources of a network device. The apparatus includes a module for receiving a digital signature including an encryption code. It also includes a module for accessing a de-encryption code in electrical communication with the module for receiving; and, it includes a module for determining allowed operations associated with the digital signature.
Dr. Tal Lavian offers insightful and decisive expertise as a telecommunications expert witness and network communications expert witness.