ABSTRACT
A technique for authenticating network users is disclosed. In one exemplary embodiment, the process may be realized as a method for authenticating network users.
The method may comprise receiving, from a client device, a request for connection to a network. The process may also include evaluating a security context associated with the requested link. The method may further comprise assigning the client device one or more access privileges based at least in part on the evaluation of the security context.
Considering a security context associated with the requested connection
An Inventor: Dr. Tal Lavian
FIELD OF THE DISCLOSURE
The present disclosure generally relates to network security and, more particularly, to a technique for authenticating network users.
BACKGROUND OF THE DISCLOSURE
To prevent unauthorized access, a network must often authenticate its users to ensure that each user is who they claim to be.
Conventional user authentication methods typically involve a brief interaction between a user and a network, wherein the user provides the web with a security identifier such as a secret password, a token device, a digital certificate, a biometric key, or a combination thereof. The network then verifies the security identifier against the records of authorized users.
Conventional user authentication methods only produce a binary result—pass or fail. If a user provides a security identifier that the network cannot verify, the user will ultimately be denied access. If the user’s security identifier can be successfully verified, the user is often granted full access to the network. In some networks, each authorized user may have predetermined access privileges known as a “role.” In this network, conventional user authentication methods still produce a binary result. If the user is authenticated, they are assigned a predetermined role in the network. If the user is not shown, they will be completely locked out.
Unlike a user-provided security identifier, conventional user authentication methods typically do not consider any other factors in their decision to grant or deny access. That is, as long as a user enters a correct username and password set, the user will be given full access or a predetermined access privilege. In other words, conventional user authentication methods only care about who the user is and do not pay attention to the circumstances in which the user accesses the network. Traditional user authentication methods may make the network vulnerable to virus infections and malicious attacks. For example, a client device infected with a virus may quickly gain access to the network and put other devices at a greater risk of infection.
In addition, it is generally assumed that a network cannot trust client devices from which end-users access the network. Therefore, once a user disconnects from the web, the user’s authentication with the network expires. The next time the user attempts to access the web, the user has to be re-authenticated. Even if the user does not leave the network but moves from one part of the network to another, the user may also have to go through a re-authentication process. To a network user, re-authentication can be inconvenient and sometimes annoying. For example, when roaming within a network, in each new location, a user may have to close some networked applications, get re-authenticated, and then restart the networked applications. As a result, in-network mobility may be burdened even for a legitimate network user.
Another problem with conventional user authentication methods lies in the general requirement that a client device requesting access to a network must be compatible with the authentication scheme supported by the network. A traditional network typically supports only one particular authentication scheme, which may be based on, for example, IEEE 802.1x standard, a Media Access Control (MAC) or Internet Protocol (IP) database, or Remote Authentication Dial In User Service (RADIUS) protocol. Such a network can only authenticate a pre-configured client device to work with the network’s chosen authentication scheme. For example, a network that only supports the IEEE 802.1x standard may not be able to authenticate a client device that employs the RADIUS protocol. Some networks go even further by requiring trusted, proprietary client software to be pre-installed in client devices. These compatibility requirements block otherwise legitimate users with incompatible devices and may cause frustration or dissatisfaction in network users.
Given the above, it would be a good idea to provide a technique for authenticating network users which overcomes the above-described inadequacies and shortcomings.
SUMMARY OF THE DISCLOSURE
A technique for authenticating network users is disclosed. In one exemplary embodiment, the process may be realized as a method for authenticating network users.
The method may comprise receiving, from a client device, a request for connection to a network. The process may also include evaluating a security context associated with the requested link. The method may further comprise assigning the client device one or more access privileges based at least in part on the evaluation of the security context.
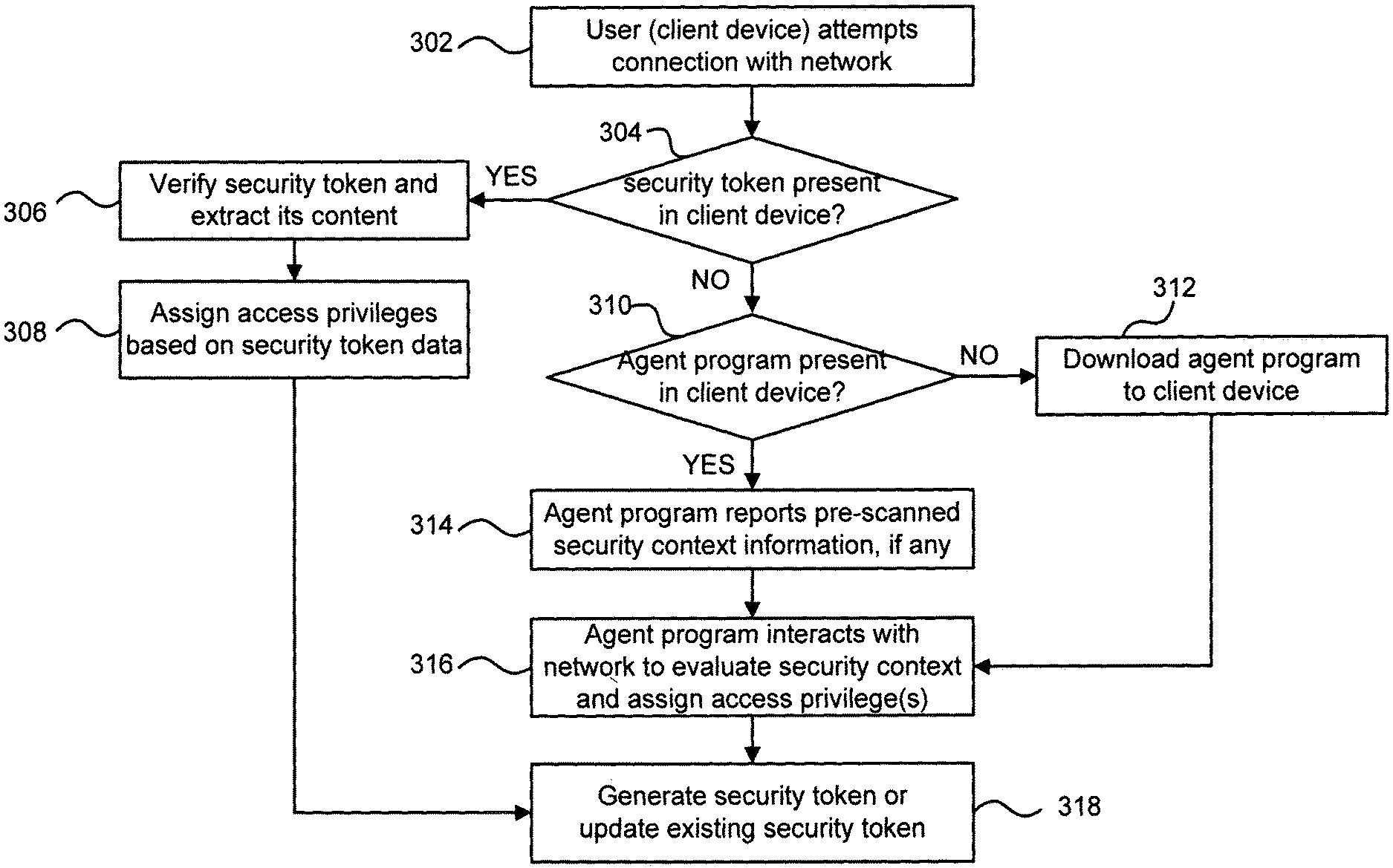
By other aspects of this particular exemplary embodiment, the security context may be evaluated at least in part by an agent program in the client device. The agent program may interact with the network to assess the security context. At least a portion of the security context may be considered before the connection request. The agent program may comprise a JAVA applet. The agent program may be automatically downloaded to the client’s device upon receipt of the connection request. In addition, the agent program may remain in the client device after the client device disconnects from the network in preparation for a subsequent connection to the network.
By further aspects of this particular exemplary embodiment, the security context may comprise one or more factors selected from a group consisting of a user login mechanism employed by the client device, a threat level associated with the network, vulnerabilities of an access medium with which the client device connects to the web, and a security level associated with the client device.
By additional aspects of this particular exemplary embodiment, the method may also include generating a security token that records the one or more access privileges assigned to the client device and storing the security token in the client device. The method may also comprise detecting the security token in the client device when the client device, after ending a first connection to the network, attempts a second connection to the network and grants the client device access to the web-based on one or more recorded access privileges if the security token is detected and verified. The first and second may connect to the network through different ports.
As a further aspect of this particular exemplary embodiment, the method may also include generating a security token that records at least a portion of the security context and storing the security token in the client device. The method may also comprise: detecting the security token in the client device when the client device, after ending a first connection to the network, attempts a second connection to the web and grants the client device access to the network based at least in part on the recorded security context if the security token is detected and verified. The recorded security context may be updated before the client device attempts the second connection to the network.
By a yet further aspect of this particular exemplary embodiment, the method may be configuring a connection between the client device and the network based at least partly on the evaluation of the security context. The method may also comprise re-configuring the relationship between the client device and the web-based, at least partly on a security token stored in the client device.
In another particular exemplary embodiment, the technique may be realized as at least one signal embodied in at least one carrier wave for transmitting a computer program of instructions configured to be readable by at least one processor for instructing at least one processor to execute a computer process for performing the method as recited above.
In yet another exemplary embodiment, the technique may be realized as at least one processor readable carrier for storing a computer program of instructions configured to be readable by at least one processor for instructing at least one processor to execute a computer process for performing the method as recited above.
In another exemplary embodiment, the technique may be realized as a system for authenticating network users. The method may comprise a network interface that facilitates communications between a client device and a network. The system may also include at least one processor that receives, from a client device, a request for connection to the network, causes a security context associated with the requested link to be evaluated and assigns the client device one or more access privileges based at least in part on the evaluation of the security context.
In another exemplary embodiment, the technique may be realized as a method for authenticating network users. The method may comprise receiving, from a client device, a request for connection to a network. The process may also include identifying a communication protocol employed by the client device. The method may further comprise adopting an authentication scheme compatible with the communication protocol if the network’s consistent authentication scheme is available to authenticate the client device. The process may also consist of downloading an agent program to the client device if the compatible authentication scheme is unavailable. The agent program interacts with the network to authenticate the client device.
By other aspects of this particular exemplary embodiment, the compatible authentication scheme may be selected from a group consisting of authentication schemes associated with IEEE 802.1x standard, authentication schemes based on one or more Media Access Control (MAC) address lists, authentication schemes based on one or more Internet Protocol (IP) address lists, and authentication schemes based on Remote Authentication Dial In User Server (RADIUS) protocol.
The present disclosure will now be described in more detail concerning the exemplary embodiments shown in the drawings I’ve included here. While the present disclosure is described below concerning exemplary embodiments, it seems that it is not limited. Those of ordinary skill in the art having access to the teachings herein will recognize additional implementations, modifications, and embodiments, as well as other fields of use, which are within the scope of the present disclosure as described herein, and concerning which the present disclosure may be of significant utility.
Dr. Tal Lavian offers insightful and decisive expertise as a telecommunications expert witness and network communications expert witness.