ABSTRACT
Deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level
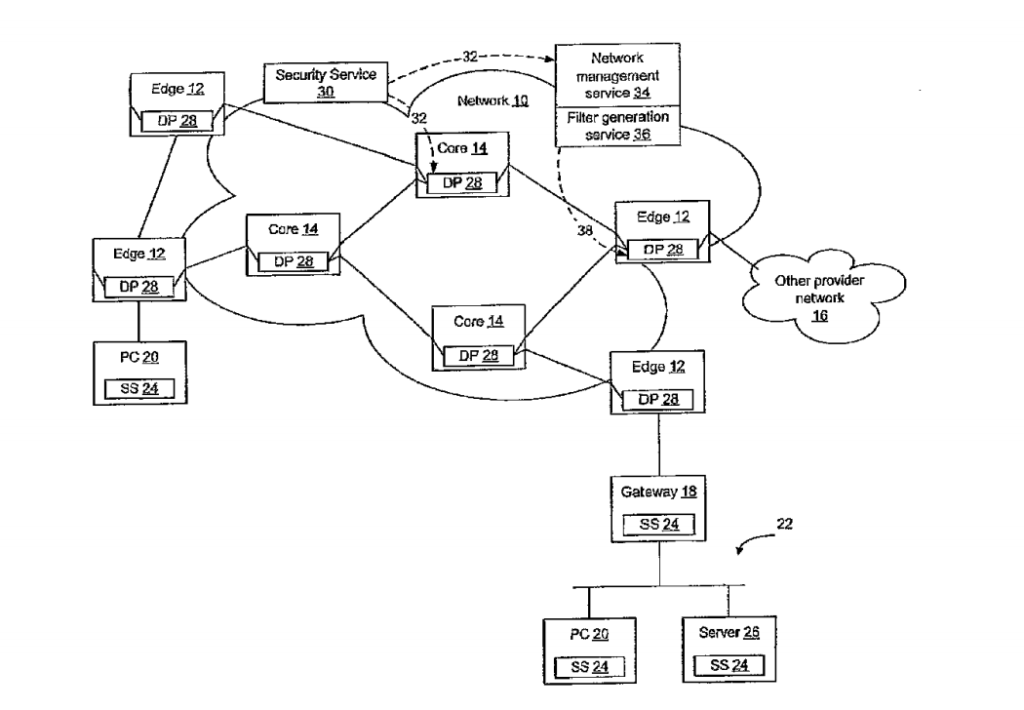
Network elements (12, 14) that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level.
As new threats are identified by a security service (30), new patterns may be created for those threats, and the new patterns may then be passed out onto the network in real time. The real-time availability of patterns enables filter rules derived from the patterns to be applied by the network elements (12, 14) so that malicious code may be filtered on the network before it reaches the end-users (20). The filter rules may be derived by security software (28) resident in the network elements or may be generated by a filter generation service configured to generate network element specific filter rules for those network elements (12, 14) that are to be implemented as detection points on the network.
Method and apparatus for network immunization
An Inventor: Dr. Tal Lavian
FIELD OF THE INVENTION
The present invention relates to the protection of communication networks and, more particularly, to a method and apparatus for network immunization.
Description of the Related Art
Data communication networks may include various routers, switches, bridges, hubs, and other network devices coupled to and configured to pass data to one another.
These devices will be referred to herein as “network elements.” Data is communicated through the data communication network by passing protocol data units, such as Internet Protocol (IP) packets, Ethernet frames, data cells, segments, or other logical associations of bits/bytes of data, between the network elements by utilizing one or more communication links between the devices. A particular protocol data unit may be handled by multiple network elements and cross multiple communication links as it travels between its source and its destination over the network.
Malicious code such as computer viruses, Trojan horses, worms, and other malicious code is commonly developed to exploit weaknesses in security measures implemented on computer systems. Malicious code may cause personal information to be collected, may take over control of the infected computer, for example, to cause the computer to begin sending out numerous email messages, or may cause numerous other actions to occur. Since malicious code may prevent a user from using their computer and may cause serious security problems, it has become common to implement security software designed to block malicious code from being able to be installed and run on the end personal computers.
There are several ways in which security software has been implemented to date. For example, security software may be implemented on a personal computer, by installing personal firewall software, antivirus software, anti-spyware software, and other types of software designed to protect the personal computer in real time. To enable this software to protect against the latest threats, the malicious code definitions (patterns) need to be updated periodically. Due to the frequency with which new versions of malicious code are developed, it may be necessary to update the malicious code patterns daily or several times per day.
Similarly, security software may be implemented in a server or gateway, either at the ingress to the network or at the egress from the network, so that the traffic being handled by that device is able to be scanned for the presence of malicious code. For example, an email server may be provided with security software that will enable it to scan all incoming or outgoing email traffic and attachments to check for the presence of a computer a virus, or other malicious code in the body of the email or in the attachment. If it appears that malicious code may be present, the email or attachment may be blocked by the email server and not transmitted to the intended recipient. In this manner, the flow of malicious code may be blocked by end-users or servers associated with the end networks to reduce the ability of the malicious code to carry out the nefarious intent of its creator. Similarly, an ISP email server may scan emails sent by its users to detect for the presence of malicious code and block any such email from continuing on the network.
Preventing malicious code at the destination personal computer level is only possible if every destination personal computer is running security software that has updated malicious code definitions. Where a computer is not running security software or the definitions in use on the computer are not up-to-date, a new security threat may get past the security software to compromise the security of the computer. Running security software at the server level is generally able to stop particular threats that are carried on traffic that passes that particular server. For example, a security software package on an ingress or egress email server may reduce the number of viruses transmitted via email. However, security software on an email server will not operate to prevent other types of security threats, such as viruses or other malicious code spread via cookies or in other ways over the Internet. Accordingly, it would be advantageous to provide a more comprehensive solution to prevent the spread of malicious code before it is able to reach the destination servers and destination personal computers.
Summary of the Invention
Immunizing Computer Networks – network elements are configured to implement prevention devices on the network, so that threats may be detected and blocked at the network level.
A method and apparatus for immunizing the network are disclosed in which network elements are configured to implement prevention devices on the network, so that threats may be detected and blocked at the network level.
According to an embodiment of the invention, the network elements forming the network that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code. The patterns may be implemented as filter rules on network elements so that the malicious code may be filtered out at the network level. As new threats are identified by a security service, new patterns are created for those threats and the new patterns are passed out onto the network in real-time, so that the filter rules associated with the patterns may be applied by the network elements. The implementation of network elements as protection devices may prevent the spread of newly detected malicious code before it has a chance to arrive at the end computer device. The patterns may be used to generate filter rules which include layer 4-7 information, as well as layer 2/3 information, so that content filtering may be performed in addition to filtering on characteristics identifiable from the packet header. Optionally, by enabling patterns to extend across multiple protocol data units, it may be possible to prevent malicious code spanning protocol data units from being transmitted on the network.
The network elements implementing the protection devices may include software configured to translate the patterns into filter rules so that, when a pattern is generated, the network elements may generate filter rules to be applied by the network elements to filter for the pattern. Alternatively, the patterns may be sent to a filter generation service configured to receive the patterns identified by the security service and translate the patterns into filter rules for use by the network elements implementing the detection points on the network. The filter rules may then be passed to the network elements for implementation on the network in a manner similar to how other filter rules are passed to these network elements so that separate security software need not be run on the network elements to enable them to be configured as detection points on the network.